The history of large and impactful cyber attacks on healthcare is well known. Of the seven biggest data breaches of 2015, three directly targeted healthcare organizations: Excellus BlueCross BlueShield, compromising 10 million records; Premera Blue Cross, affecting 11 million records; and Anthem Blue Cross, which compromised 78.8 million highly sensitive patient records.
This was just the beginning of the healthcare cyber crime tsunami that has emerged in 2016.
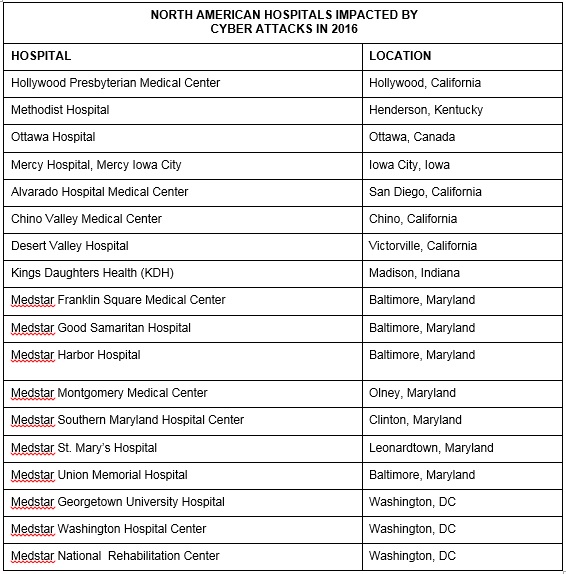
During the first few months of 2016, the healthcare industry experienced a massive wave of unprecedented cyber threats -- often imposed by organized crime -- that impacted numerous hospitals across North America. Some of these affected hospitals are listed in Table 1 - North American Hospitals Impacted by Cyber Attackers in 2016 below. And all of these attacks were mentioned in both traditional and online news media.
Cyber criminals turn to healthcare industry
It's no secret that the healthcare industry continues to be hit hard with sophisticated and destructive assaults while vastly unequipped and underprepared to defend itself. Attack methods vary -- some attackers focus on short term gain through techniques such as ransomware; others on significant long term gain through the stealthy theft of patient data.
The surge of attacks against hospitals and medical organizations makes economic sense. Medical records have between 10 to 20 times the value of credit card data, while cyber-attackers know that healthcare networks are extremely vulnerable and offer a substantial reward. As a result, the risk of being attacked has never been higher for the medical industry.
The wealth of information within a medical record allows criminals to recreate an entire identity. However, this requires significant focused effort by attackers, as well as a long-term time commitment that can often last months. Altogether, copious amounts of time are required for attackers to engineer one or more attack vectors, deploy the attacks and successfully penetrate the healthcare networks. Then the attackers must move laterally within the networks, find the critical patient records and quietly exfiltrate the data without alerting security operations or information technology teams. And while the attackers don't want all of this patient data, they often cannot differentiate between the various files, thus taking all of the material, remaining quiet within the networks for several months in order to do so.
This continued access into the network is often supplied through a MEDJACK attack vector, which sets up a backdoor within a medical device. MEDJACK -- or medical device hijack -- leverages the vulnerability of medical devices to establish and maintain "backdoors" within a healthcare enterprise. TrapX has found multiple backdoors in large healthcare institutions that were established from within numerous medical devices that provide access to cyber attackers for months prior to detection. Legacy cyber defense software often misses attacker movement through networks, giving perpetrators a secure and invisible foothold from which to explore internal networks and steal data.
In addition, most hospital teams are poorly equipped to prevent and detect these attacks. Legacy cyber security tools are often ineffective at finding active attackers breaching medical devices, while security teams face challenges when installing local suites of cyber defense software onto healthcare systems. What's more, the healthcare institution's security operations and IT teams have no access to the medical devices' internal software -- regulations mandate the manufacturer to block external access to these devices, which require FDA approval because they could be adversely affected by changes to the executables running in them.
Ransomware offers new twist to healthcare attacks
Recently, ransomware has gained substantial visibility in the wake of multiple attacks on hospital systems. Often leveraged to generate income quickly for cyber criminals, ransomware generally copies original files, encrypts them and then deletes the originals, propagating rapidly through the healthcare institution until they are stopped. This year, a destructive strain of ransomware dubbed Locky infected computers within several healthcare facilities in the United States, New Zealand, and Germany, propagating through spam emails that included malicious Microsoft Office documents. These malicious attachments, in turn, contained macros or JavaScript files that downloaded the ransomware-Locky files when activated.
In addition, another type of ransomware, known as Samas, is being used to compromise healthcare networks. In this case, the malware propagates itself through Web servers that exhibit the necessary vulnerabilities. Once the Web server is compromised, attackers use the Samas ransomware files to infect the organization's networks. Ransomware such as Samas or Locky may also be deployed after patient data has already been stolen, and if an attacker has sufficient network access, they can deliver this one-two punch fairly easily.
While not clearly visible in the public domain, these multi-faceted attacks are present in a variety of healthcare accounts. The reason? Healthcare institutions are attractive targets because of the ease in which they can be compromised. The typical hospital contains a multitude of internet-connected systems and medical devices, while the large majority of physician's practices also have electronic medical records (EMR/EHR) systems interconnected with the rest of the network -- all of which create a highly connected community that brings vulnerable medical devices together with high value patient data. Meanwhile, doctors continually access data between the networks at the hospital, the diagnostic lab, the skilled nursing facilities and their physician networks. All it takes is one infected email attachment for an attacker to establish a backdoor, find and steal data, or use automated tools to set a ransomware attack in motion.
Preventing the next hospital attack
Despite an upsurge of sophisticated attacks, medical organizations can apply numerous precautions and best practices aimed at minimizing the risk of successful attacks leveraging ransomware and MEDJACK. These strategies include enhanced employee training, especially around email files with macro executables. Access to personal email and browsing on the internet are the two common entry points for attackers and a large percentage of email contains malware either in the form of a URL that either contains malicious attachments or redirects users to a malware-laden website. Attackers also enter hospital networks by embedding URLs in the text of an email and tricking users into clicking, socially engineering the message so that it appears to be from someone within the organization or that the employee knows.
Ransomware like Locky and Samas, as well as numerous other attacks, move very quickly, so it's imperative that healthcare IT teams respond equally as fast. In response to these threats, all computing resources need to be shut down and isolated -- ideally via automation -- to prevent the spread of the malware and continued attacker access.
Perhaps the single most important shift in thinking is to assume that cyber attackers will continuously breach security defenses over time. For hospital administrators, that means imagining a world where attackers continuously breach their networks during the normal course of business.
Subsequently, next-generation technologies have emerged to combat these threats and defend healthcare institutions with new world best practices. One of those, deception technology, is a new category of cyber security designed to identify and block malicious software, targeted attacks, zero-day exploits and other sophisticated threats in real-time before any damage can be done. Among other things, deception technology provides a broad scale deployment of camouflage decoys and lures onto the network that are intermingled with the hospital's real information technology resources. The decoys appear identical in every way to the hospital's real assets and are designed to be attractive to attackers moving stealthily within a network in search of high-value assets. The attackers are immediately caught the moment they touch one of the decoys.
Some types of deception technology also isolate the attacker's malware tools and deliver a full report directly to the hospital IT team, allowing security professionals to initiate remediation and removal. That said, many hospitals should also enlist help from specialized Managed Security Service Providers (MSSPs) for comprehensive threat prevention and security services, which have the necessary resources and staffing to fight these new threats.
In summary, healthcare networks remain an attractive and easy target for cyber attackers. Healthcare data will remain a target of choice for hackers because of its tremendous -- and growing -- value. New best practices wrapped around emerging technologies such as deception can provide a powerful option for healthcare institutions by deceiving and misdirecting the attackers, reducing the time to breach detection and then defeating the attackers, allowing the healthcare organization to rapidly return to normal operations.
The views, opinions and positions expressed within these guest posts are those of the author alone and do not represent those of Becker's Hospital Review/Becker's Healthcare. The accuracy, completeness and validity of any statements made within this article are not guaranteed. We accept no liability for any errors, omissions or representations. The copyright of this content belongs to the author and any liability with regards to infringement of intellectual property rights remains with them.

